Risks of wireless networks
For homes and businesses that operate wireless networks security can be a concern. This is because anyone within range of the signal can connect to an open wireless network. It is difficult to identify who is on the network.
Data may be intercepted by hackers as it is broadcast through the air on radio waves.
Mitigating wireless risks
There are a number of things you can do to mitigate the risks of wreless networks, such as:
Changing the SSID: the SSID is the name of your router and default names can be the same on many routers giving you the chance you have the same SSID as one of your neighbours whch could lead to security issues as devices
confuse the networks.
Using a password: By applying a strong password to the wireless network only those who know the password will be able to gain access.
Using a MAC address whitelist: a MAC address is an address hard coded into devices at the point of manufacture to uniuely identify them. A MAC address whitelist is a list of the MAC addresses of devices that are allowed to use
the network. All others are denied.
Using approrpiate encryption: Encryption scrambles data before it is sent and unscrambles it when it is received meaning hackers cannot read data they can pluck out of the air as it is transmitted. Encryption standards continue
to develop in response to more sophisticated threats.
Acceptable use
Public wi-fi networks are generally restricted in terms of content that can and can't be accessed. A local takeaway would not want its customers accessing adult content which might be seen by young patrons. Companies offering
free wi-fi need to make clear the conditions for its use including not using it to commit cyber crimes or look at content unsuitable for the environment. There may also be restrictions on the length of time users can be connected
or the amount of bandwidth they can use.
'Evil twin' hotspots
'Evil twin' hotspots are wi-fi hotspots that look like legitimate free wi-fi access points but are actually duplicates. These are run by hackers to carry out 'man in the middle' attacks. An evil twin can be set up from just
about any portable device and the hacker can move closer to their intended victims to increase the signal strength making it seem a more attractive proposition. They are most common in places with large public wi-fi networks.
When you connect to an 'Evil Twin' hotspot the hacker has full control of that wireless access point. Any data you send goes via the hacker so they can observe and steal login credentials for any sites that you visit while
connected.
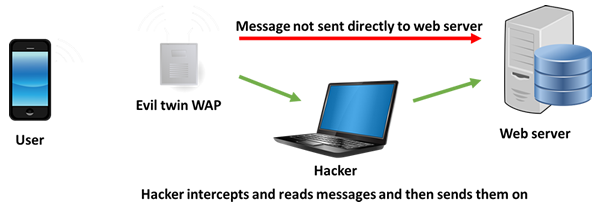
To stay away from 'evil twin' hotspots always avoid unsecured networks. You will be warned by your device if you try to join an unsecured network. This means it is not using encryption. Do not ignore warning messages. For
sensitive data think about using your own data allowance. You should also think about what sites you visit using public wi-fi. It is also possible to use a VPN with a portable device for an extra layer if security.