Protecting against malware
Anti-malware software is the primary defence against malware. It works because it has a database of known malware and scans your computer checking for the existence of these.
Modern anti-malware also has a range of other protections such monitoring for suspicious app activity and giving alerts about potentially dangerous websites before user visit them.
It is only as good as its last update as newer threats will not be identifiable.
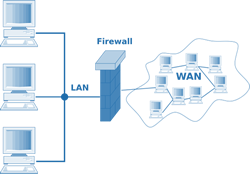
Firewalls are another defence against malware. A firewall sits between a network and the internet and can be configured to say what type of data may enter from the internet and
what may be sent out. This can prevent various types of malware from entering your system in the first place.
Protecting against social engineering
The primary defence against social engineering is training. It is the number one type of attack against computer systems and networks and only increasing in frequency and
sophistication. Consistent policies should be laid out for all types of communication.

Protecting against brute force attacks
Having a set number of attempts to log in before locking your account is one basic step organisations take to protect against brute force attacks. The use two factor
authentication or biometrics can further limit the ability of hackers to use a brute force attack. In addition it is essential firms enforce good password practices such as:
- Suitable length and possibly complexity
- Make users change passwords regularly e.g. every 3-6 months
- Inform
staff not to reuse passwords they use elsewhere

Preventing DOS and DDOS attacks
A DOS attack might be able to be countered by blocking the IP address from which the data flooding the network is coming. A DDOS attack is harder to stop as the data flooding
the network comes from large numbers of computers. One method used is CAPTCHAs which try to ensure requests are coming from humans. There are also professional companies, like
Cloudflare, that provide DDOS protection as a service.

Preventing data interception and theft
Encryption is the key tool to prevent data interception and theft. If data is encrypted then even if it is intercepted it will be meaningless.
User access levels can mean
that only the right people can access certain valuable information reducing the risk of sensitive data being stolen.
Suitable physical security such as locks on doors and
cameras can help prevent people accessing the network undetected.
Preventing SQL injection
There are some basic steps that can be taken when programming web forms to avoid the possibility of SQL injection. The essence is to limit the requests that can be made of the
database and filter any inputs for SQL.
